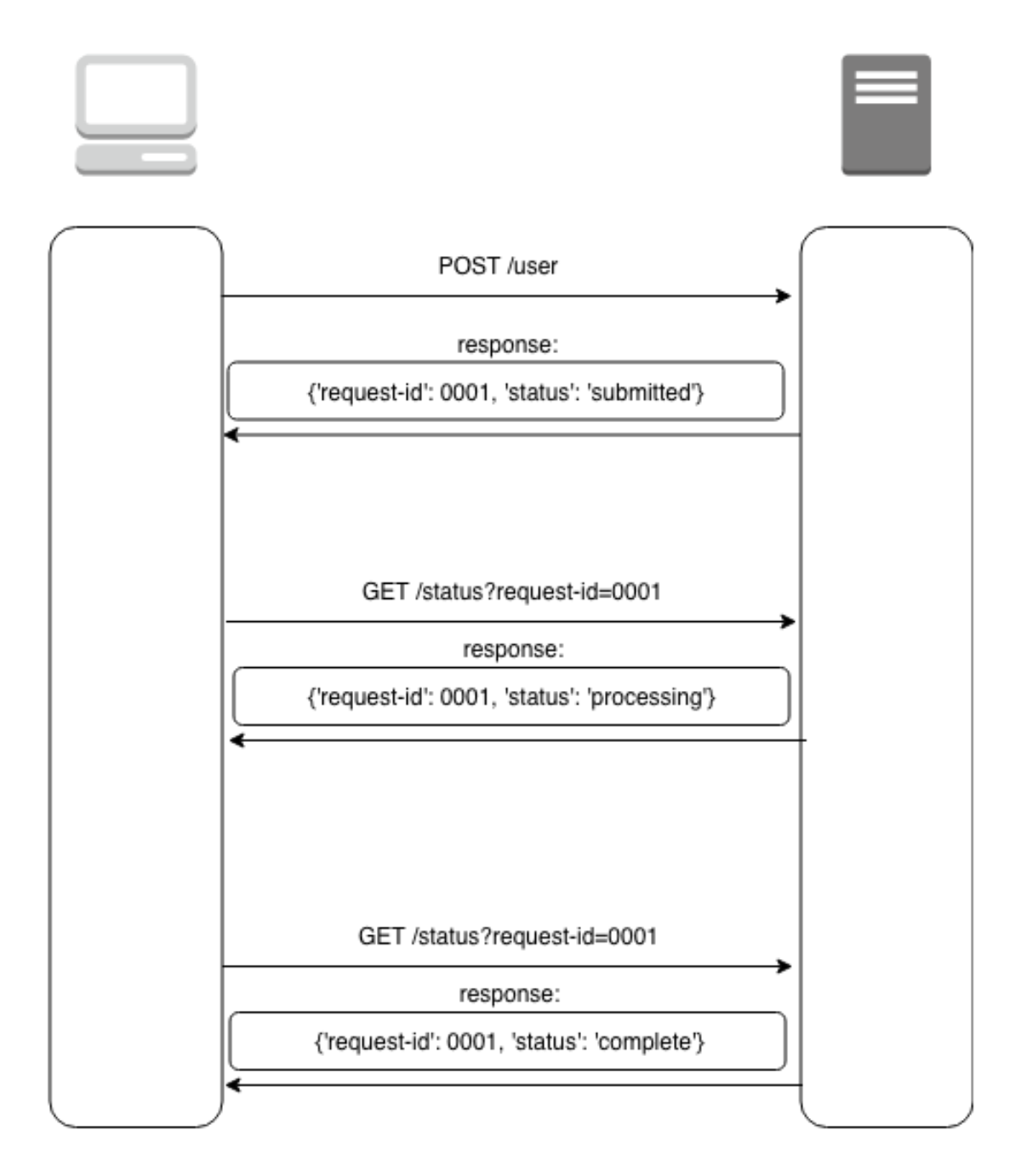
Mastering API Gateway in 105 easy steps
The Serverless 🥑 over at AWS love to tell us how great API Gateway is because it can integrate directly with so many services. I mean, look at this list.
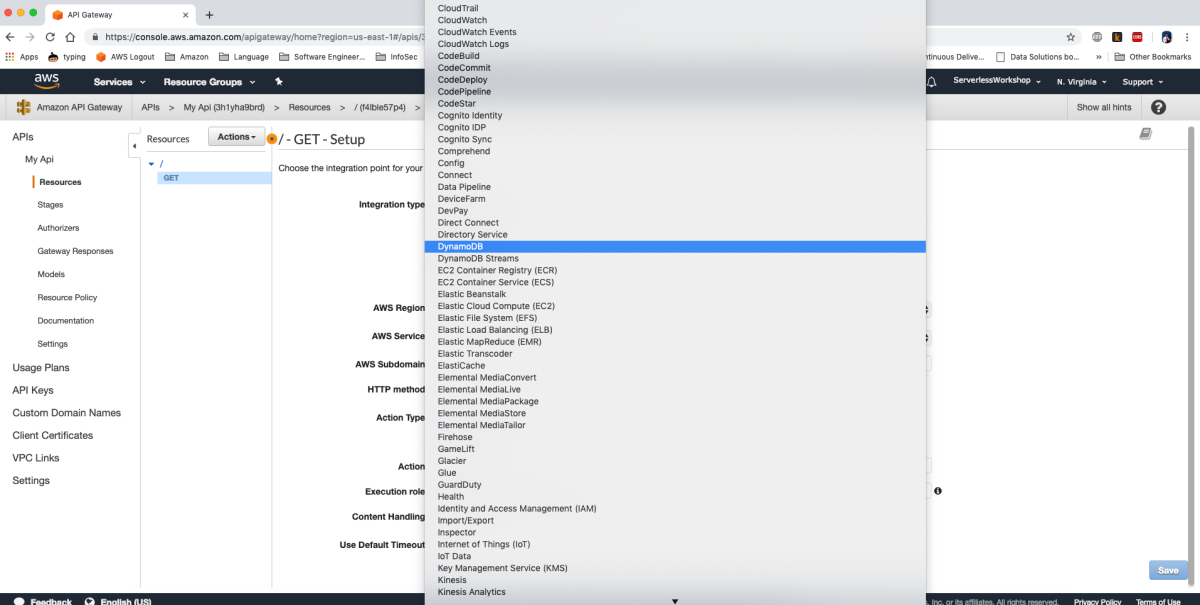
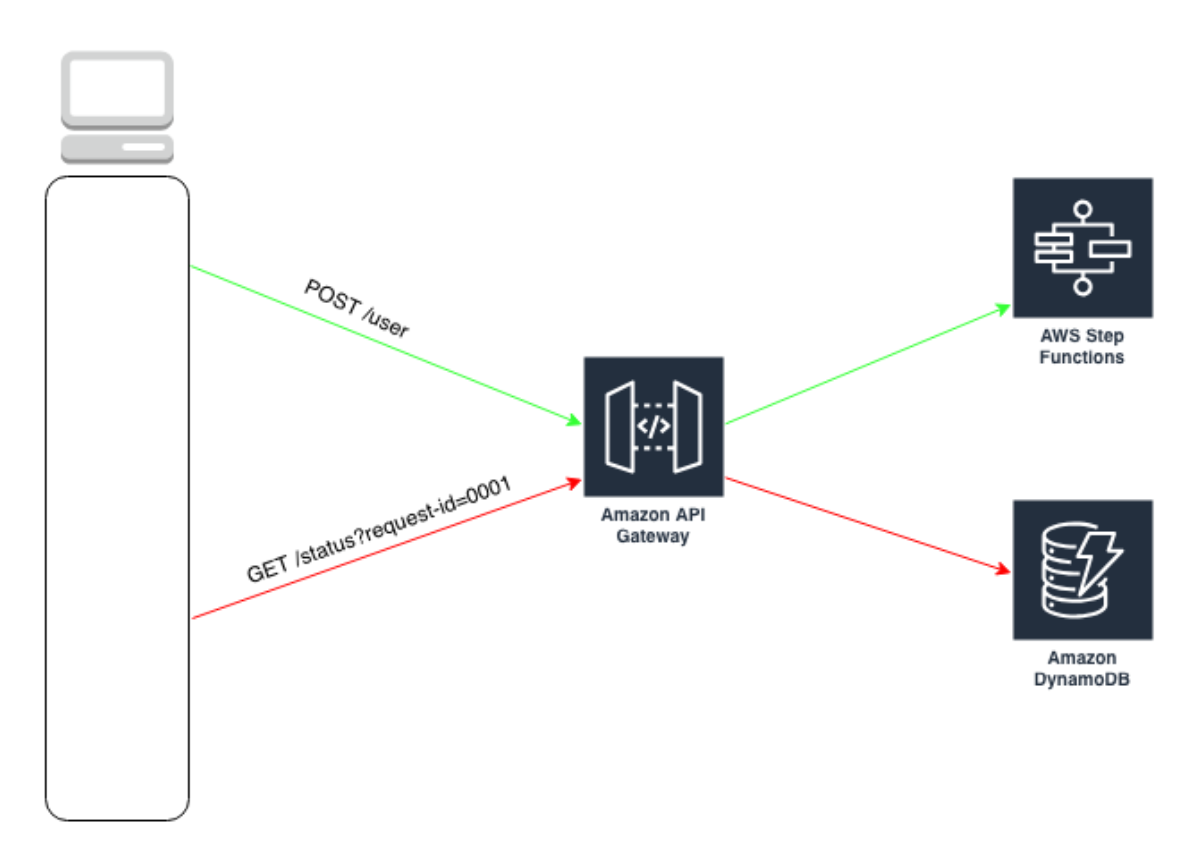
What's not to love?!? I'm going to hop right in and wire up one of these services, selected completely at random to show how easy this is. Let's go with DynamoDB because it's a great example and not at all because it already has about 1/2 million examples on blogs all over the world.

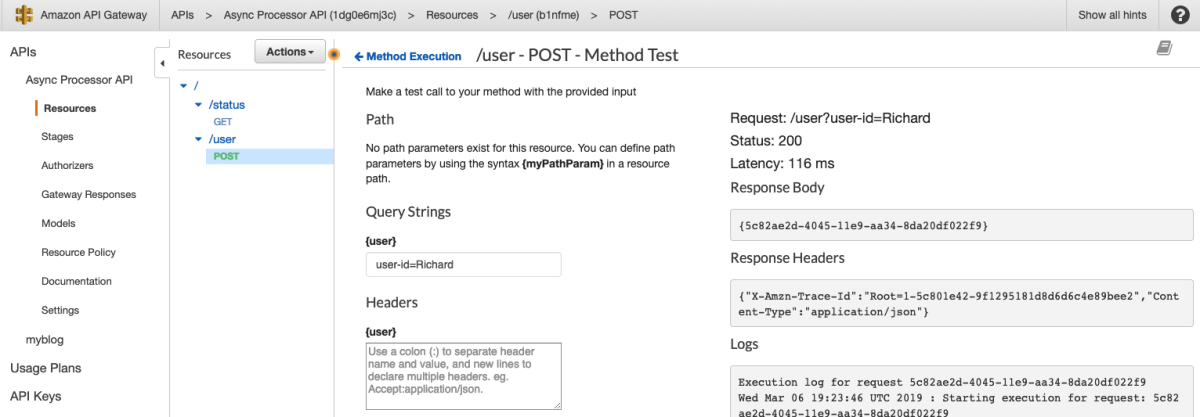
I'll just fill in this handy form

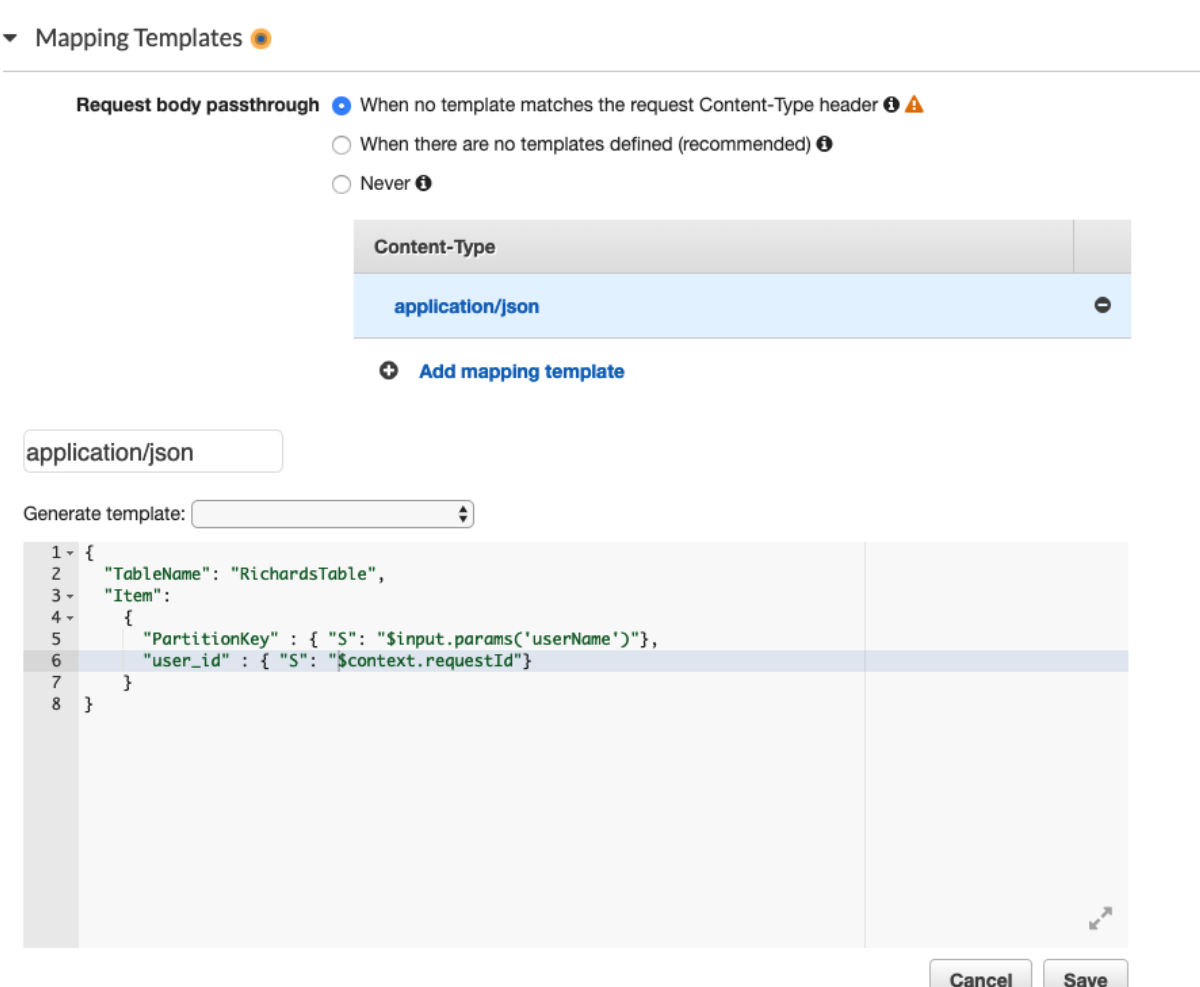
Great, now I update the mapping templates and I'm off to the races.
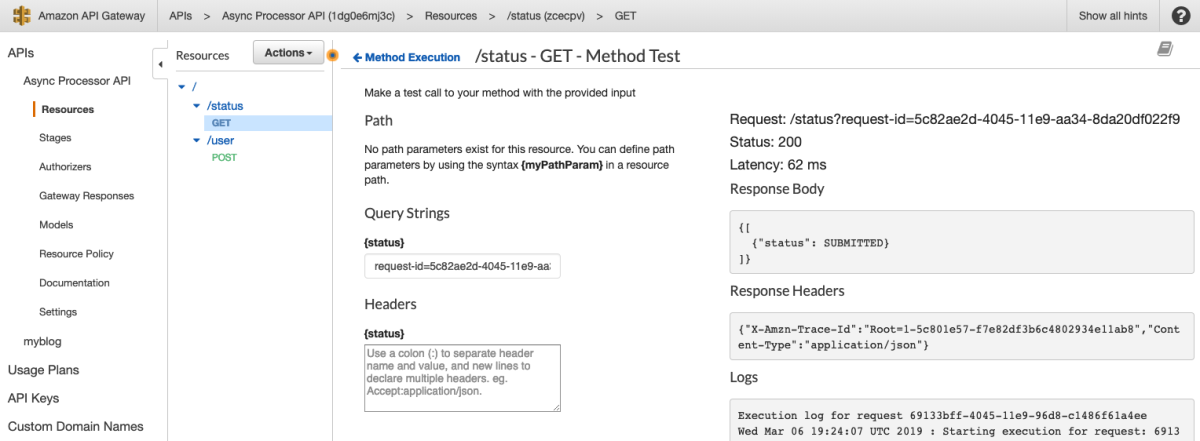
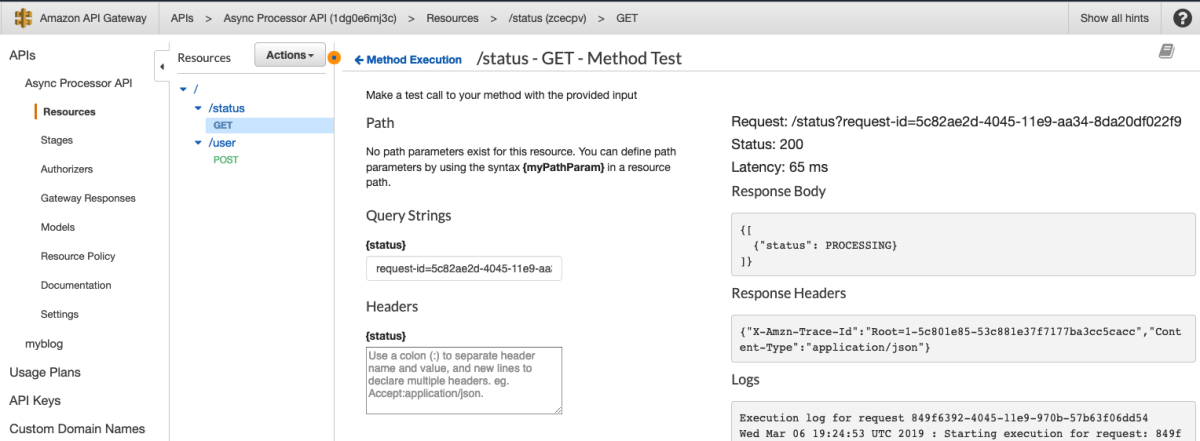
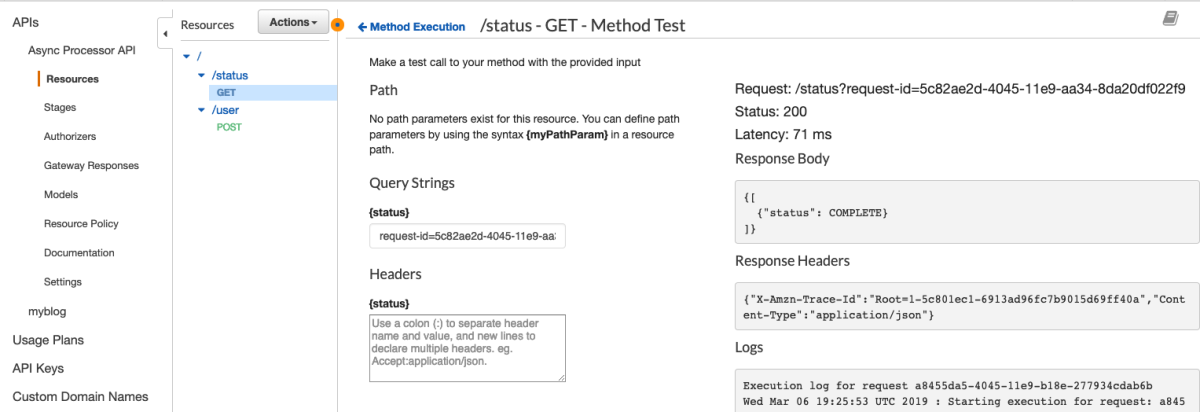
Awesome. Now let's test this.
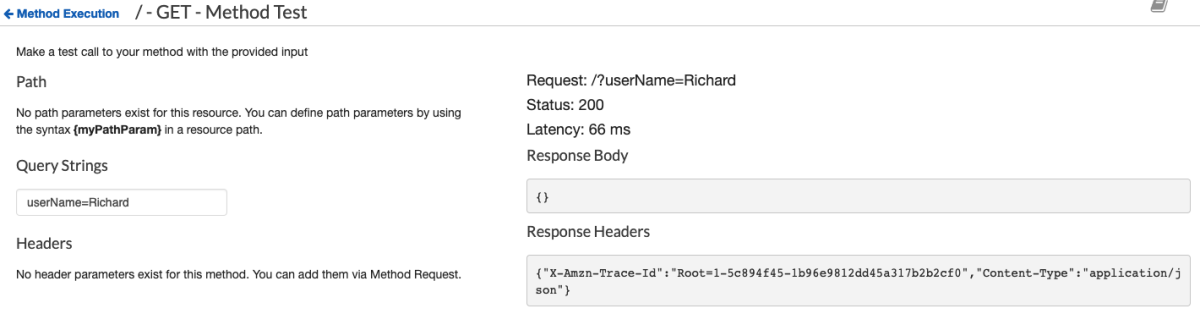
You hear that rumbling in the distance? That's the train to Flavor Town with Guy Fieri at the helm because this is some sweet API magic. I have just enough time to check Dynamo to make sure the item was put correctly before the train leaves the station.

The entire train is cheering by now, you're well on your way to not needing any lambdas to proxy requests between API Gateway and any one of those 105 services listed in the console.
This is where the Serverless 🥑 makes the statement that's the DevRel equivalent of "This can work for any service, the proof of which is left to the reader as an exercise" and you're left thinking "Why am I exercising on a train?" but here you are none the less. So you pick another service at random and try to strike out on your own. I hear AWS Athena sounds nice this time of year, let's see if we can run a query through API Gateway.

Well, Shit!!!! What's the name of the Action for starting a query in Athena?!? Let's go ask that one person who knows all these random bits of trivia.
This looks promising

"StartQueryExecution" isn't what I would expect it to be called, but it's the closest thing I can find in the list of available Actions.
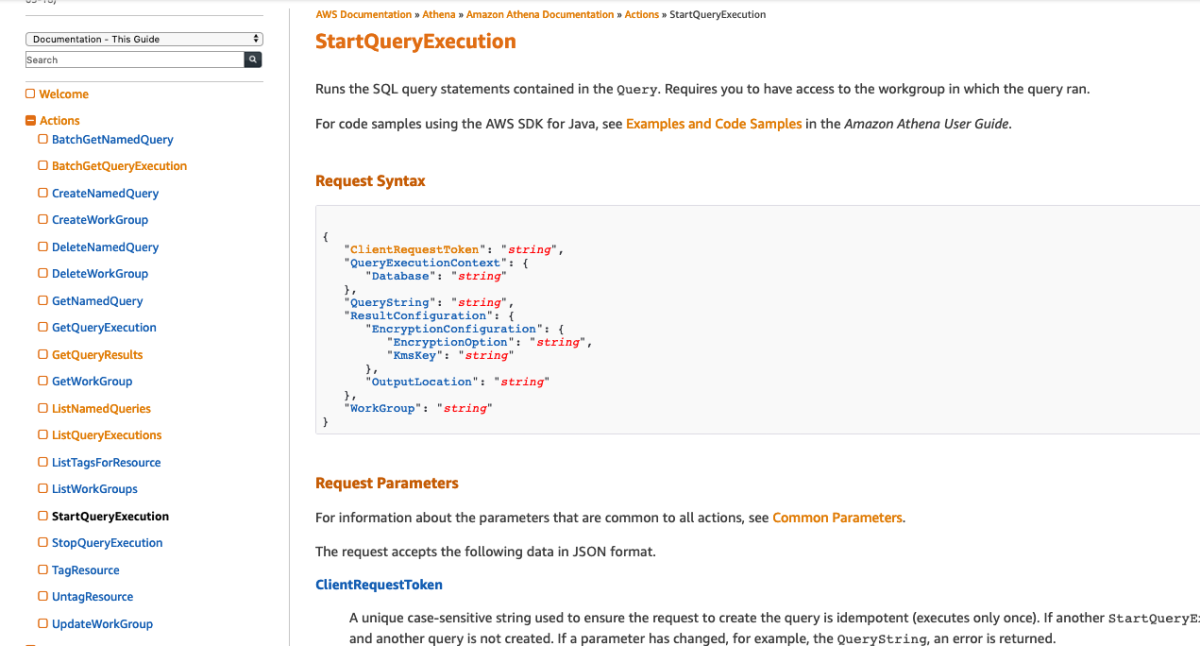
On second thought, I really don't want to have to think about all these variable while I'm trying to get this to work (I should crawl before I run). Let's find an Action that doesn't need any inputs and get that to work first, then add some complexity later. The Closest I can find is ListNamedQueries, it has some parameters but none of them are required.
Back to API Gateway. I add "ListNamedQueries" to the Action
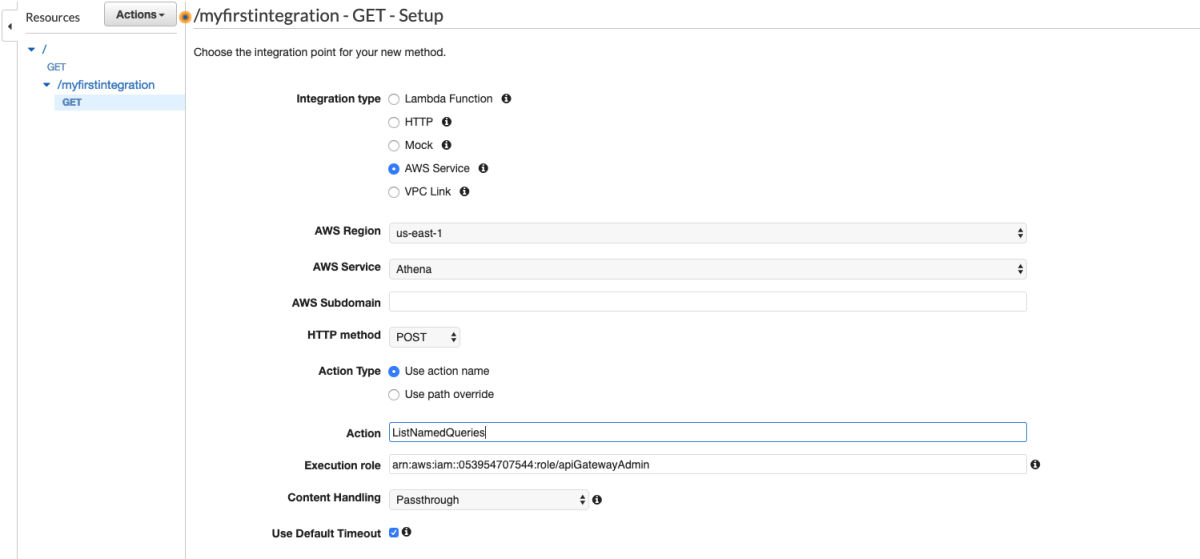
Let's give it a whirl.

HAHA, You really thought it would be that easy? You must be new to these parts. That's just great. I don't even know where to start with this. Maybe I'll check the AWS CLI and see how it looks in there.
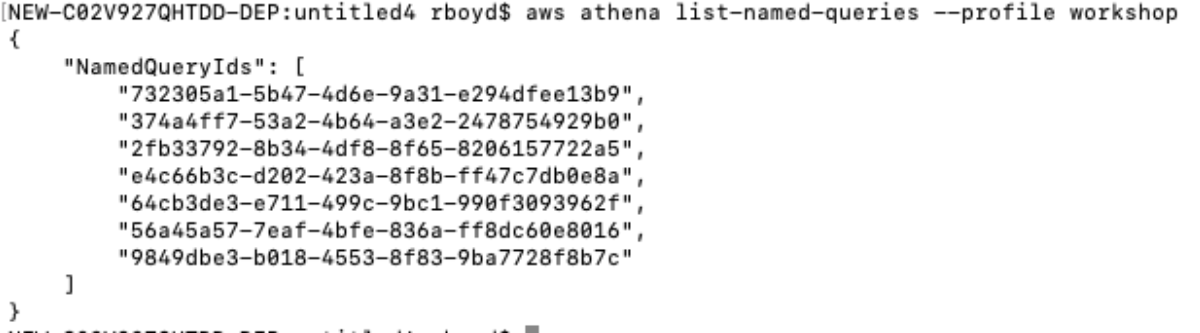
It works with no parameters from my mac, maybe the debug mode will tell me what's going on.

AH HAH!! There it is. Do you see the difference? If you're like me, you don't see it. If you're like me after about 12 hours, you still don't see the difference. If you're like me after 24 hours, 2 support tickets, and a late night email to our Technical Account Manager you still don't see the difference but you know that other people don't see the difference either. I'm going to save you all of that trouble and show you the difference.
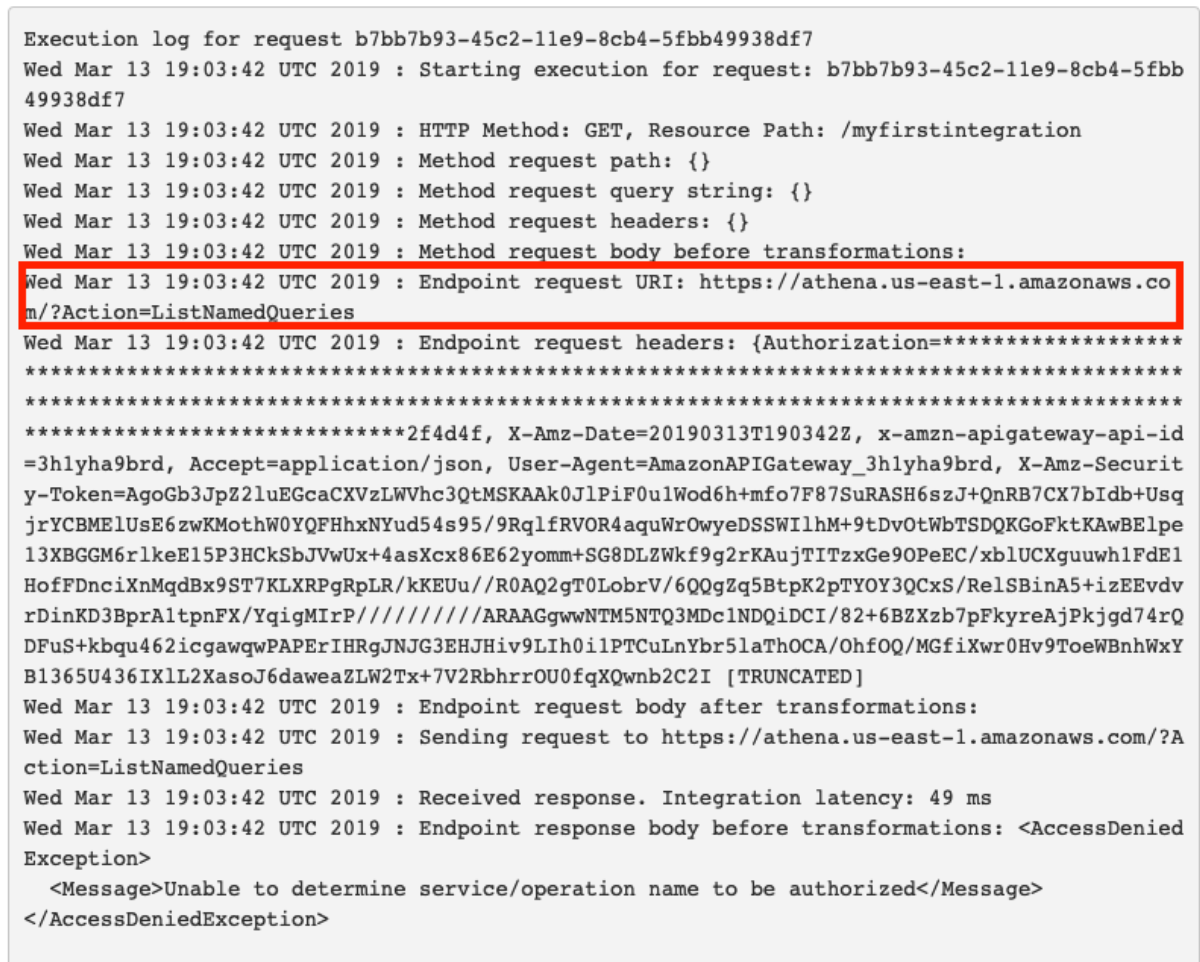
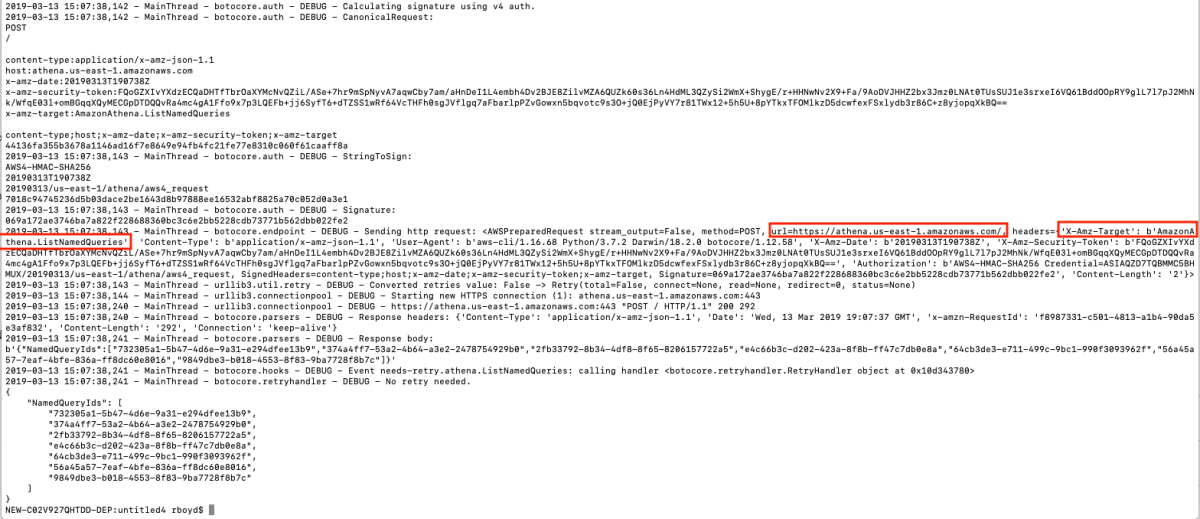
It looks like API Gateway is appending ?Action=[actionName] to the url but Athena actually expects the action specified in a Header named "X-Amz-Target". I'm arrogant enough to think I can fix this.

I've replaced the "Action" field with and empty "Path override" and added the missing header. I'm basically done so I'll just go watch cartoons instead of actually finishing this. The next morning I come into work and test it out.
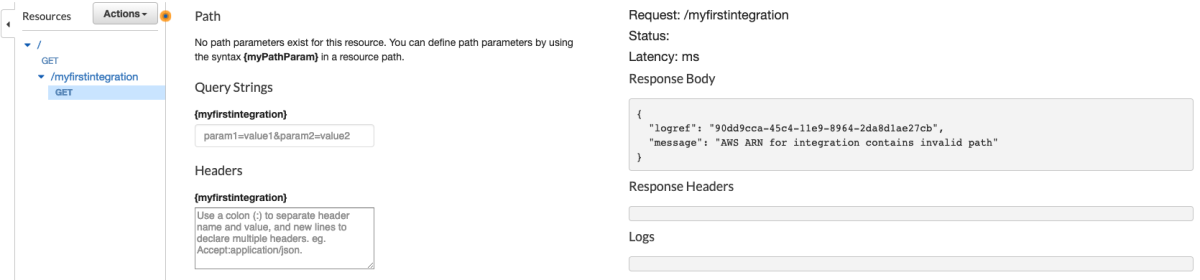
OOF!!! Maybe it needs an 'empty' Path?!?
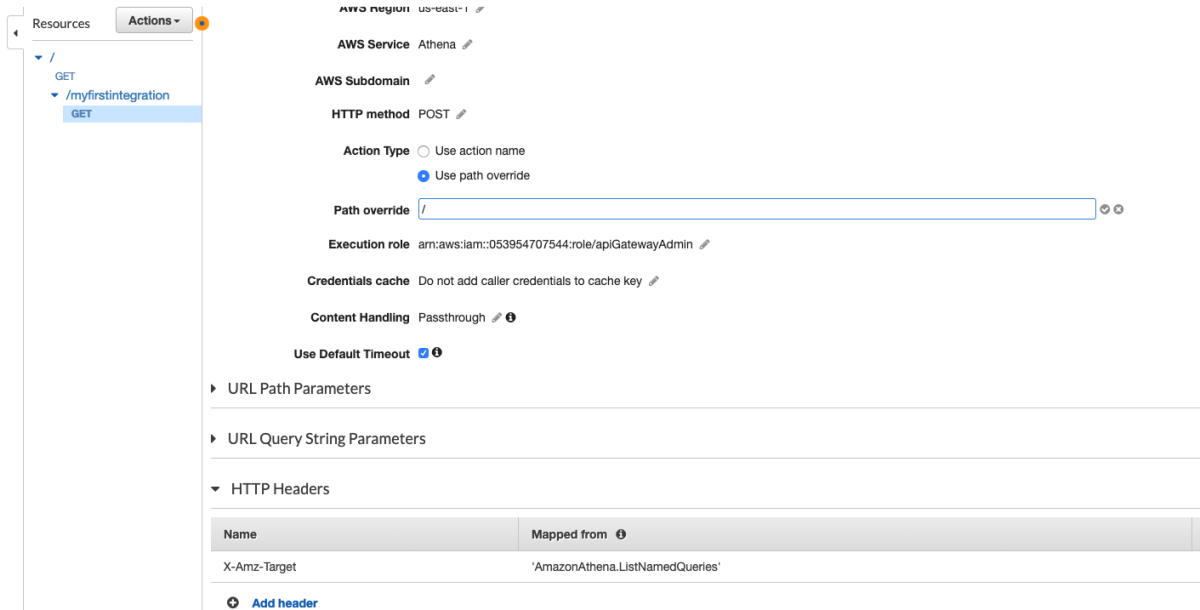
Yeah, that'll definitely fix it.
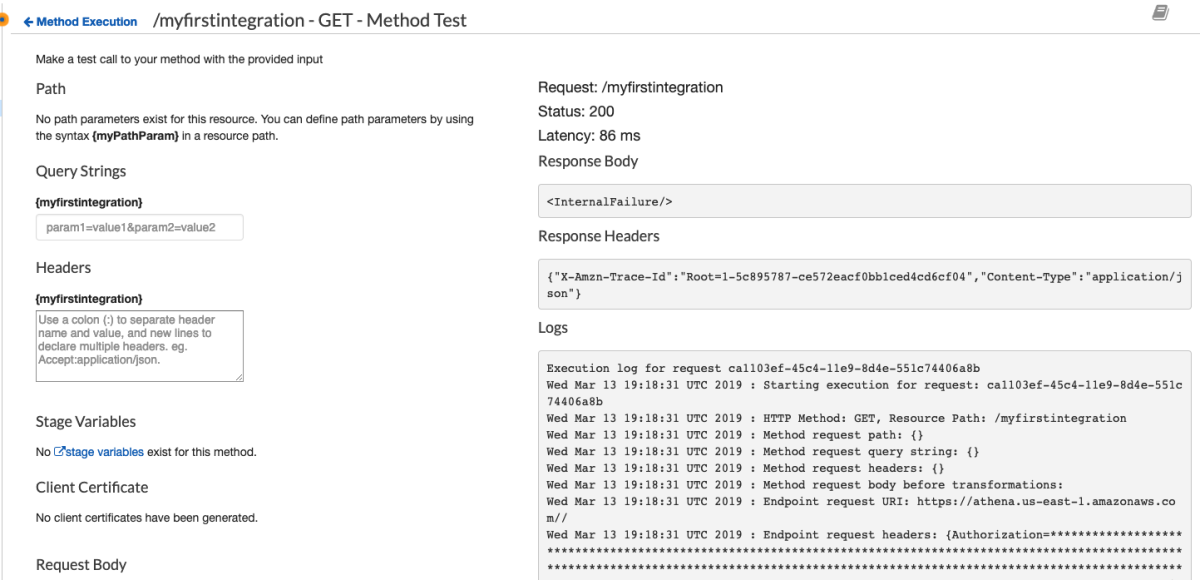
(╯°□°)╯︵ ┻━┻
It's a good thing this is serverless and I don't need to care about the internals of the managed platforms. a week goes by and I try to crack this again. I wonder what happens if I explicitly add an empty body to the request?
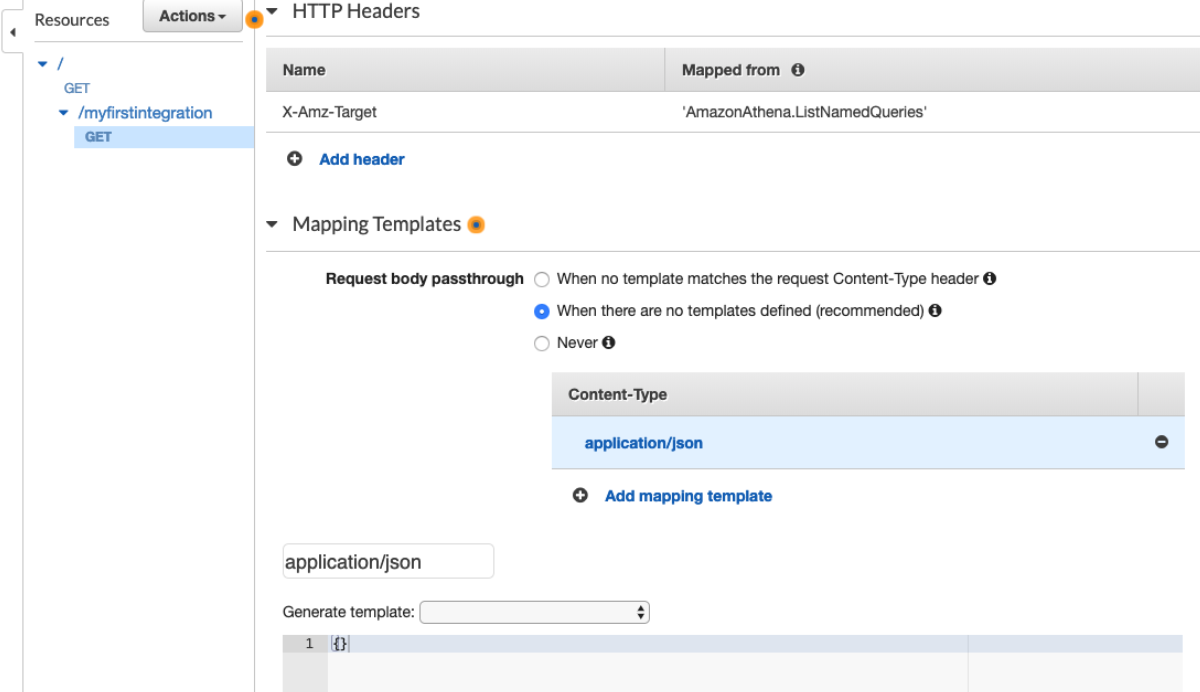
This will certainly work!!!

me > (╯°□°)╯︵ ┻━┻
┬─┬ノ( º _ ºノ) < Ben K.
me > (╯°□°)╯︵ ┻━┻
┬─┬ノ( º _ ºノ) < Ben K.
me > (╯°□°)╯︵ ┻━┻
I find a doc that outlines making HTTP requests.
https://docs.aws.amazon.com/apigateway/api-reference/making-http-requests/
This part looks promising
Specifies JSON and the version, for example, Content-Type: application/x-amz-json-1.0.
Let's see if that helps
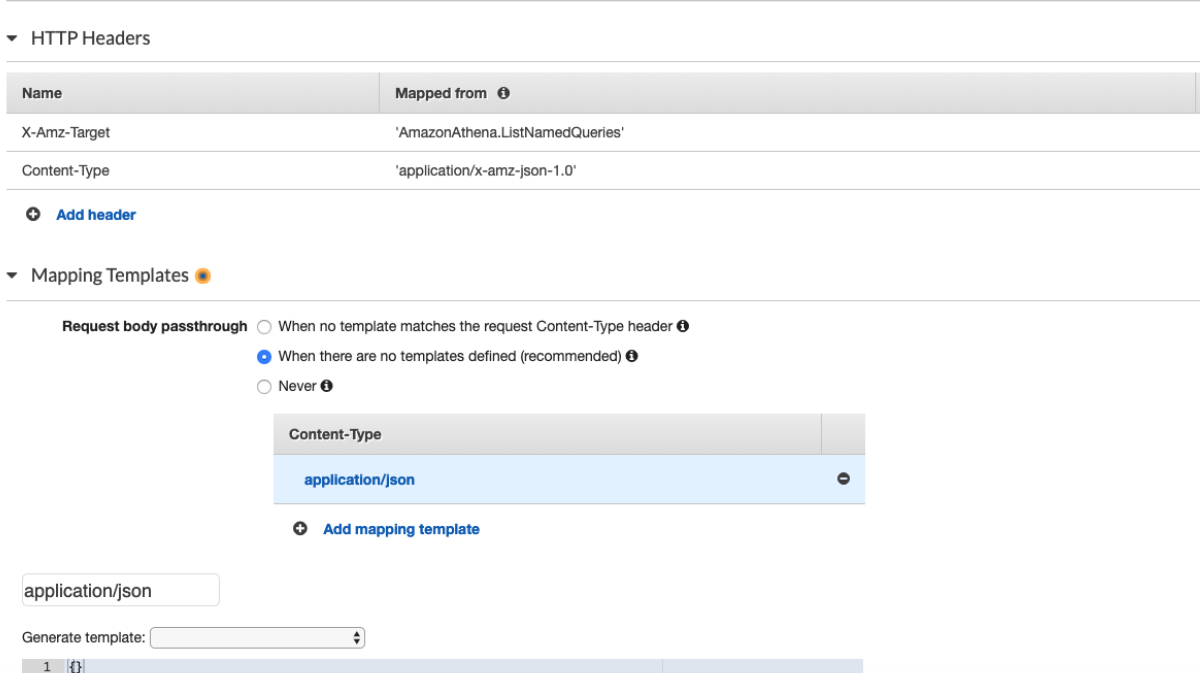
I mean, it's in the docs. IT HAS TO WORK!!!!!

(┛ಠ_ಠ)┛彡┻━┻
Okay. I think I've made the point. What you need to do is use application/x-amz-json-1.1, obviously.
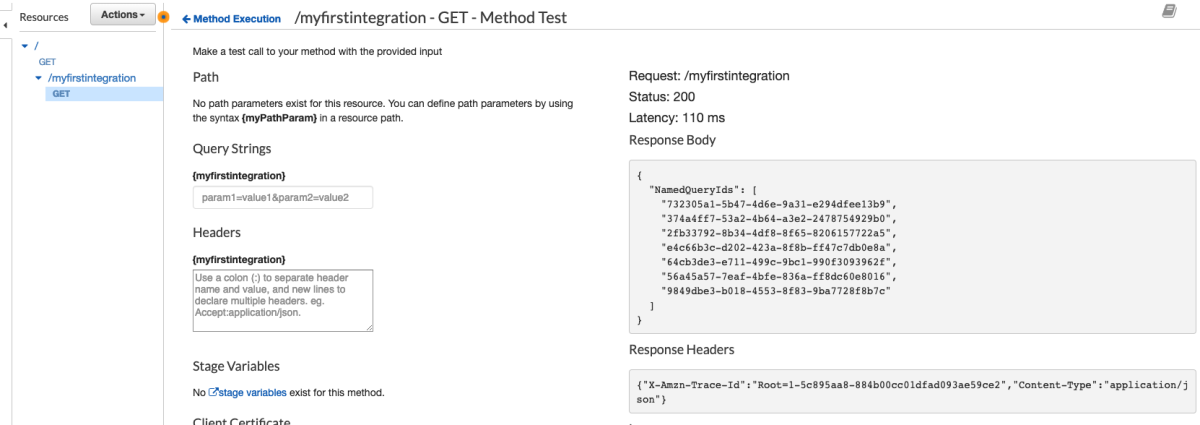
FINALLY!!!! 2 down 103 more to go.